Using IKEVIEW for VPN debugging
IKEVIEW is a Checkpoint Partner tool available for VPN troubleshooting purposes. It is a Windows executable that can be downloaded from Checkpoint.com. Ikeview was originally only available to Checkpoint's CSP partners however they will gladly supply you a copy of thie file if you have a licensed Checkpoint product. This file parses the IKE.elg file located on the firewall.
http://pingtool.org/downloads/IKEView.exe
To use IKEVIEW for VPN troubleshooting do the following:
1. From the firewall type the following:
vpn debug ikeon
This will create the IKE.elg file located in $FWDIR/log
2. Attempt to establish the VPN tunnel. All phases of the connection will be logged to the IKE.elg file.
3. SCP the file to your local desktop.
WINSCP works great
4. Launch IKEVIEW and select File>Open. Browse to the IKE.elg file.
Understanding the IKE.elg output
All Phase I packets will either be labeled Main Mode or Aggressive Mode.
Phase II packets will be labeled QM or Quick Mode.
An arrow pointing to the left (<) indicates IPSEC packets that the Checkpoint firewall (local) receives from the remote Peer. An arrow pointing to the right (>) represent IPSEC packets that the Checkpoint firewall is sending to the remote peer.
Ikeview Phase I Main Mode exchange:
If your encryption fails in Main Mode Packet 1, then you need to check your VPN proposal (encryption/hash/lifetime).
Packet 2 ( MM Packet 2 in the trace ) is from the responder to agree on one encryption and hash algorithm
Packets 3 and 4 aren’t usually used when troubleshooting. They perform key exchanges and include a large number called a NONCE. The NONCE is a set of never before used random numbers sent to the other part, signed and returned to prove the parties identity.
Packets 5 and 6 perform the authentication between the peers. The peers IP address shows in the ID field under MM packet 5. Packet 6 shows that the peer has agreed to the proposal and has authorised the host initiating the key exchange.
If your encryption fails in Main Mode Packet 5, then you need to check the authentication - Certificates or pre-shared secrets
Phase I Main Mode example:
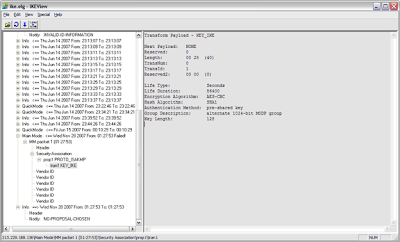
In the example below, we see that Phase I is failing after the first packet (Main mode Phase I takes 6 packets to complete). After the first packet (the initial proposal packet), we see that the remote peer responds with No Proposal Chosen. In this example, the remote peer rejected the local proposal of AES/SHA1 with a lifetime of 86400 seconds and the provided Preshared key.
 Phase II Quick Mode exchange:
Phase II Quick Mode exchange:
Next is Phase II - the IPSec Security Associations (SAs) are negotiated, the shared secret key material used for the SA is determined and there is an additional DH exchange. Phase II failures are generally due to a misconfigured VPN domain. Phase II occurs in 3 stages:
1. Peers exchange key material and agree encryption and integrity methods for IPSec.
2. The DH key is combined with the key material to produce the symmetrical IPSec key.
3. Symmetric IPSec keys are generated.
In IkeView under the IP address of the peer, expand Quick Mode packet 1:
> "P2 Quick Mode ==>" for outgoing or "P2 Quick Mode <==" for incoming > QM Packet 1
> Security Association
> prop1 PROTO_IPSEC_ESP
> tran1 ESP_AES (for an AES encrypted tunnel)
You should be able to see the SA life Type, Duration, Authentication Alg, Encapsulation Mode and Key length.
If your encryption fails here, it is one of the above Phase II settings that needs to be looked at.
There are two ID feilds in a QM packet. Under
> QM Packet 1
> ID
You should be able to see the initiators VPN Domain configuration including the type (ID_IPV4_ADDR_SUBNET) and data (ID Data field).
Under the second ID field you should be able to see the peers VPN Domain configuration.
Packet 2 from the responder agrees to its own subnet or host ID, encryption and hash algorithm.
Packet 3 completes the IKE negotiation.
Phase II Quick Mode example:
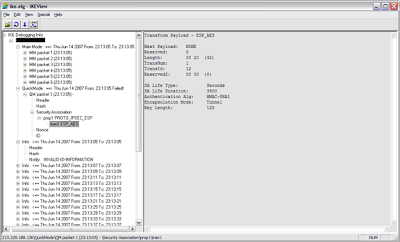
Below is a screenshot of a failed VPN connection for Phase II. From this example, we can see that Phase I(Main Mode) completed successfully. Phase II (Quick Mode) shows a Failed status.
As indicated below, there is an Outgoing proposal (local peer) for AES/SHA1 with a lifetime of 3600 seconds. After the failed Phase II packet, there is an Info packet from the remote peer indicating “Invalid ID Information”. This is an indication that the remote peer rejected our proposal. If the tunnel were being initiated on the Remote End, we would also see the remote peer’s proposal and can compare that to the local proposal.
Common errors indicated in Ikeview
No Proposal Chosen:
A common error that can be easily identified in IKEVIEW is “No Proposal Chosen”.
In the Quick Mode section that is followed by the info line displaying the “No Proposal Chosen” message should display the network mask used for the VPN handshake. Compare the mask used in the local encryption domain with the mask sent by the remote peer. This is a common error when establishing tunnels with non-Checkpoint firewalls. Checkpoint, by default, supernets networks contained in the encryption domain. The method for resolving this issue on the Checkpoint firewall differs depending on if the firewall is R55, R61 simple mode, or R61 classic mode. In R55 there is an option in the VPN section of the Interoperable firewall object that tells the Firewall for “One tunnel per pair of hosts, or one tunnel per pair of subnets”. In R61 Simple mode, there is an option in the VPN Community that says “exchange key per host”. In R61 Classic mode you will need to do the following during non-business hours:
CP Stop
Modify the $FWDIR/lib/user.def.
Change the parameter "IKE_largest_possible_subnet" from true to "false".
CP start.
Aggressive Mode failure:
Aggressive mode uses 3 packets instead of 6 during the Phase I negotiations. Therefore if 1 side of the tunnel is configured for Aggressive Mode and the other side is configured for Main Mode, the 2 peers will not agree with the contents of the first packet during the exchange. If the local peer is mistakenly configured to use Aggressive Mode (which is a less secure method), the outgoing packet will be labeled Aggressive Mode.
Invalid ID-Information:
This is an indication that the remote peer rejected either the Phase I or Phase II proposal from the local peer.
PROTO_IPCOMP in the QM packet
This is an indication that IP Compression is enabled for this tunnel.
Refer to :
https://www.cpug.org/forums/ipsec-vpn-blade-virtual-private-networks/4764-vpn-trouble-shooting.html
IKEVIEW is a Checkpoint Partner tool available for VPN troubleshooting purposes. It is a Windows executable that can be downloaded from Checkpoint.com. Ikeview was originally only available to Checkpoint's CSP partners however they will gladly supply you a copy of thie file if you have a licensed Checkpoint product. This file parses the IKE.elg file located on the firewall.
http://pingtool.org/downloads/IKEView.exe
To use IKEVIEW for VPN troubleshooting do the following:
1. From the firewall type the following:
vpn debug ikeon
This will create the IKE.elg file located in $FWDIR/log
2. Attempt to establish the VPN tunnel. All phases of the connection will be logged to the IKE.elg file.
3. SCP the file to your local desktop.
WINSCP works great
4. Launch IKEVIEW and select File>Open. Browse to the IKE.elg file.
Understanding the IKE.elg output
All Phase I packets will either be labeled Main Mode or Aggressive Mode.
Phase II packets will be labeled QM or Quick Mode.
An arrow pointing to the left (<) indicates IPSEC packets that the Checkpoint firewall (local) receives from the remote Peer. An arrow pointing to the right (>) represent IPSEC packets that the Checkpoint firewall is sending to the remote peer.
Ikeview Phase I Main Mode exchange:
If your encryption fails in Main Mode Packet 1, then you need to check your VPN proposal (encryption/hash/lifetime).
Packet 2 ( MM Packet 2 in the trace ) is from the responder to agree on one encryption and hash algorithm
Packets 3 and 4 aren’t usually used when troubleshooting. They perform key exchanges and include a large number called a NONCE. The NONCE is a set of never before used random numbers sent to the other part, signed and returned to prove the parties identity.
Packets 5 and 6 perform the authentication between the peers. The peers IP address shows in the ID field under MM packet 5. Packet 6 shows that the peer has agreed to the proposal and has authorised the host initiating the key exchange.
If your encryption fails in Main Mode Packet 5, then you need to check the authentication - Certificates or pre-shared secrets
Phase I Main Mode example:
In the example below, we see that Phase I is failing after the first packet (Main mode Phase I takes 6 packets to complete). After the first packet (the initial proposal packet), we see that the remote peer responds with No Proposal Chosen. In this example, the remote peer rejected the local proposal of AES/SHA1 with a lifetime of 86400 seconds and the provided Preshared key.
 Phase II Quick Mode exchange:
Phase II Quick Mode exchange:Next is Phase II - the IPSec Security Associations (SAs) are negotiated, the shared secret key material used for the SA is determined and there is an additional DH exchange. Phase II failures are generally due to a misconfigured VPN domain. Phase II occurs in 3 stages:
1. Peers exchange key material and agree encryption and integrity methods for IPSec.
2. The DH key is combined with the key material to produce the symmetrical IPSec key.
3. Symmetric IPSec keys are generated.
In IkeView under the IP address of the peer, expand Quick Mode packet 1:
> "P2 Quick Mode ==>" for outgoing or "P2 Quick Mode <==" for incoming > QM Packet 1
> Security Association
> prop1 PROTO_IPSEC_ESP
> tran1 ESP_AES (for an AES encrypted tunnel)
You should be able to see the SA life Type, Duration, Authentication Alg, Encapsulation Mode and Key length.
If your encryption fails here, it is one of the above Phase II settings that needs to be looked at.
There are two ID feilds in a QM packet. Under
> QM Packet 1
> ID
You should be able to see the initiators VPN Domain configuration including the type (ID_IPV4_ADDR_SUBNET) and data (ID Data field).
Under the second ID field you should be able to see the peers VPN Domain configuration.
Packet 2 from the responder agrees to its own subnet or host ID, encryption and hash algorithm.
Packet 3 completes the IKE negotiation.
Phase II Quick Mode example:
Below is a screenshot of a failed VPN connection for Phase II. From this example, we can see that Phase I(Main Mode) completed successfully. Phase II (Quick Mode) shows a Failed status.
As indicated below, there is an Outgoing proposal (local peer) for AES/SHA1 with a lifetime of 3600 seconds. After the failed Phase II packet, there is an Info packet from the remote peer indicating “Invalid ID Information”. This is an indication that the remote peer rejected our proposal. If the tunnel were being initiated on the Remote End, we would also see the remote peer’s proposal and can compare that to the local proposal.

Common errors indicated in Ikeview
No Proposal Chosen:
A common error that can be easily identified in IKEVIEW is “No Proposal Chosen”.
In the Quick Mode section that is followed by the info line displaying the “No Proposal Chosen” message should display the network mask used for the VPN handshake. Compare the mask used in the local encryption domain with the mask sent by the remote peer. This is a common error when establishing tunnels with non-Checkpoint firewalls. Checkpoint, by default, supernets networks contained in the encryption domain. The method for resolving this issue on the Checkpoint firewall differs depending on if the firewall is R55, R61 simple mode, or R61 classic mode. In R55 there is an option in the VPN section of the Interoperable firewall object that tells the Firewall for “One tunnel per pair of hosts, or one tunnel per pair of subnets”. In R61 Simple mode, there is an option in the VPN Community that says “exchange key per host”. In R61 Classic mode you will need to do the following during non-business hours:
CP Stop
Modify the $FWDIR/lib/user.def.
Change the parameter "IKE_largest_possible_subnet" from true to "false".
CP start.
Aggressive Mode failure:
Aggressive mode uses 3 packets instead of 6 during the Phase I negotiations. Therefore if 1 side of the tunnel is configured for Aggressive Mode and the other side is configured for Main Mode, the 2 peers will not agree with the contents of the first packet during the exchange. If the local peer is mistakenly configured to use Aggressive Mode (which is a less secure method), the outgoing packet will be labeled Aggressive Mode.
Invalid ID-Information:
This is an indication that the remote peer rejected either the Phase I or Phase II proposal from the local peer.
PROTO_IPCOMP in the QM packet
This is an indication that IP Compression is enabled for this tunnel.
Refer to :
https://www.cpug.org/forums/ipsec-vpn-blade-virtual-private-networks/4764-vpn-trouble-shooting.html
350 comments
«Oldest ‹Older 201 – 350 of 350 Newer› Newest»-
Anonymous
said... @
October 1, 2024 at 5:45 AM

-
-
Bhumi Goswami
said... @
October 2, 2024 at 6:46 AM

-
-
Sadhvi
said... @
October 18, 2024 at 4:05 AM

-
-
Data Analytics Courses In Ontario
said... @
October 20, 2024 at 1:29 AM

-
-
NEHA PATHARE
said... @
October 25, 2024 at 3:10 AM

-
-
Evd
said... @
October 26, 2024 at 11:59 AM

-
-
Anonymous
said... @
October 27, 2024 at 9:28 AM

-
-
Sadhvi
said... @
October 29, 2024 at 3:59 AM

-
-
Data science Courses in Norwich
said... @
November 5, 2024 at 6:58 AM

-
-
Data Analytics Courses In Ontario
said... @
November 17, 2024 at 9:52 AM

-
-
Data Analytics Courses In Ontario
said... @
November 19, 2024 at 1:22 AM

-
-
P. Zaheer Khan
said... @
November 20, 2024 at 8:24 AM

-
-
Richa
said... @
November 20, 2024 at 9:23 PM

-
-
Jatin Tyagi
said... @
November 20, 2024 at 11:07 PM

-
-
Sabha Singh
said... @
November 21, 2024 at 12:54 AM

-
-
RICHA
said... @
November 21, 2024 at 9:57 PM

-
-
P. Zaheer Khan
said... @
November 22, 2024 at 11:49 PM

-
-
Prachi IIMskills
said... @
November 26, 2024 at 5:42 AM

-
-
AI Readers club
said... @
November 26, 2024 at 7:10 AM

-
-
Golden Vape
said... @
November 29, 2024 at 2:46 AM

-
-
Reena Solanki
said... @
December 14, 2024 at 8:14 AM

-
-
Bloomsdale
said... @
December 16, 2024 at 4:27 AM

-
-
data science
said... @
December 20, 2024 at 4:12 AM

-
-
Sadhvi
said... @
December 24, 2024 at 3:35 AM

-
-
jeh aditi
said... @
December 26, 2024 at 7:42 AM

-
-
Intern Neel
said... @
December 26, 2024 at 9:31 AM

-
-
Sadhvi
said... @
December 31, 2024 at 12:36 AM

-
-
Shikha iimskills
said... @
January 1, 2025 at 11:34 AM

-
-
Gautham34
said... @
January 2, 2025 at 6:48 AM

-
-
Reena kuwar
said... @
January 6, 2025 at 9:27 PM

-
-
Data Science Courses In Micronesia
said... @
January 7, 2025 at 7:20 PM

-
-
Data Science Courses In Micronesia
said... @
January 10, 2025 at 6:24 AM

-
-
Shikha IIMSKILLS
said... @
January 14, 2025 at 11:18 AM

-
-
NEHA PATHARE
said... @
January 15, 2025 at 11:34 PM

-
-
iim skills Diksha
said... @
February 1, 2025 at 12:21 AM

-
-
KASHISH IIM SKILLS
said... @
February 5, 2025 at 10:52 PM

-
-
maziniimskills
said... @
February 8, 2025 at 4:37 AM

-
-
Chanda
said... @
February 9, 2025 at 7:59 PM

-
-
Chanda
said... @
February 9, 2025 at 8:06 PM

-
-
sanjana
said... @
March 1, 2025 at 9:34 PM

-
-
sanjana
said... @
March 3, 2025 at 2:08 AM

-
-
Judith
said... @
March 7, 2025 at 6:10 AM

-
-
Judith
said... @
March 9, 2025 at 10:16 PM

-
-
IIMskills ( Premkumar vattanavar)
said... @
March 13, 2025 at 3:14 AM

-
-
IIM SKILLS (Pushpa)
said... @
March 24, 2025 at 7:03 PM

-
-
mohd shoeab
said... @
March 25, 2025 at 3:15 PM

-
-
mohd shoeab
said... @
March 26, 2025 at 4:54 AM

-
-
IIM SKILLS (Pushpa)
said... @
March 26, 2025 at 6:31 AM

-
-
Abdush Samad
said... @
March 26, 2025 at 3:22 PM

-
-
Abdush Samad
said... @
March 27, 2025 at 8:53 AM

-
-
tushar kaushik
said... @
March 30, 2025 at 10:34 PM

-
-
Monisha
said... @
April 1, 2025 at 4:28 PM

-
-
tushar kaushik
said... @
April 2, 2025 at 12:50 AM

-
-
MedicalCodingCoursesinvaranasi
said... @
April 3, 2025 at 6:28 AM

-
-
Ayush
said... @
April 6, 2025 at 1:11 AM

-
-
Thrisha
said... @
April 6, 2025 at 8:40 AM

-
-
Keerthi
said... @
April 6, 2025 at 11:46 AM

-
-
IIM SKILL Yashaswi
said... @
April 6, 2025 at 11:59 AM

-
-
Harsh
said... @
April 8, 2025 at 12:17 AM

-
-
Keerthi
said... @
April 9, 2025 at 4:09 AM

-
-
IIM SKILL Yashaswi
said... @
April 11, 2025 at 9:50 AM

-
-
Thrisha
said... @
April 12, 2025 at 10:18 AM

-
-
MedicalCodingCoursesinvaranasi
said... @
April 17, 2025 at 6:27 AM

-
-
laungh new ipad pro
said... @
April 18, 2025 at 10:11 AM

-
-
rani iimskills
said... @
April 23, 2025 at 7:57 AM

-
-
Sarah
said... @
April 23, 2025 at 11:02 PM

-
-
Mitali
said... @
April 26, 2025 at 9:59 AM

-
-
Mitali
said... @
April 29, 2025 at 9:32 AM

-
-
Mitali
said... @
April 29, 2025 at 10:56 AM

-
-
GajenderIIM
said... @
May 4, 2025 at 8:38 AM

-
-
Aisha Duhailij
said... @
May 6, 2025 at 8:11 AM

-
-
Anonymous
said... @
May 7, 2025 at 12:43 AM

-
-
Anonymous
said... @
May 7, 2025 at 5:21 AM

-
-
Hkblog25
said... @
May 10, 2025 at 10:35 AM

-
-
Kennady Skyappz Academy
said... @
May 13, 2025 at 1:42 AM

-
-
Hkblog25
said... @
May 14, 2025 at 4:40 AM

-
-
GajenderIIM
said... @
May 15, 2025 at 2:58 AM

-
-
Aditya Shankar
said... @
May 21, 2025 at 12:09 AM

-
-
jitendra
said... @
May 22, 2025 at 11:37 AM

-
-
PathToSuccess
said... @
May 23, 2025 at 5:36 AM

-
-
Elakhiya
said... @
May 23, 2025 at 11:50 PM

-
-
harshgoswami
said... @
May 24, 2025 at 4:00 AM

-
-
harshgoswami
said... @
May 24, 2025 at 4:03 AM

-
-
digital.cvm.2@gmail.com
said... @
May 24, 2025 at 5:41 AM

-
-
sree st
said... @
May 24, 2025 at 5:42 AM

-
-
digital.cvm.2@gmail.com
said... @
May 25, 2025 at 3:53 AM

-
-
Elakhiya
said... @
May 25, 2025 at 9:32 AM

-
-
PathToSuccess
said... @
May 26, 2025 at 12:17 PM

-
-
harshgoswami
said... @
May 26, 2025 at 1:25 PM

-
-
FLK
said... @
May 26, 2025 at 8:04 PM

-
-
Kajal95
said... @
June 25, 2025 at 12:33 AM

-
-
Kajal95
said... @
June 26, 2025 at 11:31 PM

-
-
Saloni
said... @
July 7, 2025 at 1:13 AM

-
-
Arpita ah
said... @
July 8, 2025 at 7:55 AM

-
-
Saloni
said... @
July 9, 2025 at 6:31 AM

-
-
IIM Skills(Neha Tiwari)
said... @
July 9, 2025 at 11:46 PM

-
-
Arpita ah
said... @
July 10, 2025 at 2:01 AM

-
-
kirti
said... @
July 11, 2025 at 9:37 AM

-
-
IIM Skills(Neha Tiwari)
said... @
July 12, 2025 at 12:21 AM

-
-
Anonymous
said... @
July 12, 2025 at 3:27 AM

-
-
kirti
said... @
July 12, 2025 at 8:52 AM

-
-
Meghna
said... @
July 13, 2025 at 12:17 AM

-
-
Dimple
said... @
July 14, 2025 at 12:54 AM

-
-
Tushar gautam
said... @
July 14, 2025 at 8:09 AM

-
-
Tushar gautam
said... @
July 15, 2025 at 12:29 PM

-
-
tanishqa921
said... @
July 16, 2025 at 3:46 AM

-
-
iimskill priya
said... @
July 16, 2025 at 10:18 AM

-
-
Meghna
said... @
July 17, 2025 at 7:42 AM

-
-
iimskill priya
said... @
July 17, 2025 at 8:44 AM

-
-
Medical coding courses in Delhi
said... @
July 18, 2025 at 3:02 AM

-
-
tanishqa921
said... @
July 18, 2025 at 10:22 AM

-
-
Anonymous
said... @
July 19, 2025 at 2:11 AM

-
-
Hima Rasheed
said... @
July 21, 2025 at 3:42 AM

-
-
GAUTAM0
said... @
July 22, 2025 at 6:58 AM

-
-
Medical coding courses in Delhi
said... @
July 22, 2025 at 10:41 PM

-
-
Dimple
said... @
July 26, 2025 at 10:59 AM

-
-
Asif
said... @
August 4, 2025 at 12:08 AM

-
-
princy jain
said... @
August 5, 2025 at 7:44 AM

-
-
Bhavika
said... @
August 7, 2025 at 1:39 AM

-
-
princy jain
said... @
August 7, 2025 at 2:42 AM

-
-
Bhavika
said... @
August 8, 2025 at 1:49 AM

-
-
Priti Saha
said... @
August 8, 2025 at 4:40 AM

-
-
IIM Skills
said... @
August 8, 2025 at 11:26 AM

-
-
akashiimskill
said... @
August 8, 2025 at 10:51 PM

-
-
Sohail Digi
said... @
August 9, 2025 at 12:01 AM

-
-
Nilabh
said... @
August 9, 2025 at 3:59 AM

-
-
akashiimskill
said... @
August 9, 2025 at 8:32 AM

-
-
IIM Skills
said... @
August 9, 2025 at 11:25 AM

-
-
Sohail Digi
said... @
August 10, 2025 at 4:59 AM

-
-
Monika Khatnani
said... @
August 10, 2025 at 6:59 PM

-
-
Nilabh
said... @
August 11, 2025 at 7:29 AM

-
-
Priti Saha
said... @
August 12, 2025 at 5:15 AM

-
-
Monika Khatnani
said... @
August 12, 2025 at 8:14 AM

-
-
iim.skills
said... @
August 14, 2025 at 2:00 AM

-
-
IIM Skills(Shreya Saha)
said... @
August 17, 2025 at 9:20 AM

-
-
indu
said... @
August 21, 2025 at 9:12 AM

-
-
indu
said... @
August 23, 2025 at 10:49 AM

-
-
Best Software Institute Hyd
said... @
September 18, 2025 at 2:30 AM

-
-
Sanjana
said... @
November 9, 2025 at 9:53 PM

-
-
sravanthi
said... @
November 19, 2025 at 7:58 PM

-
-
sravanthi
said... @
November 19, 2025 at 8:30 PM

-
-
ONLINE IT GURU
said... @
January 2, 2026 at 8:26 PM

-
-
vr
said... @
January 4, 2026 at 7:07 AM

-
-
ONLINE IT GURU
said... @
January 5, 2026 at 2:54 AM

-
-
ONLINE IT GURU
said... @
January 6, 2026 at 2:56 AM

-
-
ONLINE IT GURU
said... @
January 6, 2026 at 2:58 AM

-
-
ONLINE IT GURU
said... @
January 27, 2026 at 10:30 PM

-
-
ONLINE IT GURU
said... @
January 27, 2026 at 10:40 PM

-
-
ONLINE IT GURU
said... @
January 27, 2026 at 10:43 PM

-
-
ONLINE IT GURU
said... @
January 27, 2026 at 10:45 PM

-
«Oldest ‹Older 201 – 350 of 350 Newer› Newest»Great read! Your insights sparked my curiosity and encouraged me to think critically about the topic. I especially liked your examples—they really illustrated your points well. Thanks for sharing
Online Data Science Course
I appreciate the troubleshooting tips you've included; they can save a lot of time and frustration. Great job
Data science courses in Bhutan
This is an incredibly helpful guide for troubleshooting VPN issues with IKEVIEW. The breakdown of Phase I and Phase II packets, as well as common errors like "No Proposal Chosen" and "Invalid ID Information," makes the process of analyzing VPN connections much clearer.
Data science courses in Mysore
"This article on the Data Science Course in Dadar is very enlightening!
The course content looks engaging and relevant to current industry needs.
I appreciate the breakdown of what students can expect to learn.
It’s encouraging to see such strong programs available locally.
I’ll definitely consider this course for my career advancement!"
"I took IIM Skills’ Data science while living in Mumbai, and it has been fantastic. The online format fits seamlessly into my schedule."
I appreciate how you connected various ideas throughout the post. It creates a richer understanding and encourages readers to think critically about the relationships involved
Data science courses in Mumbai
The post on the Check Point Firewall Blog about troubleshooting Check Point VPNs is very helpful! It provides clear, practical steps for diagnosing and resolving common VPN issues. The insights into log analysis and configuration checks are particularly valuable for network administrators. Thanks for sharing such useful troubleshooting tips!
Data science courses in Bangalore.
IKEVIEW is definitely a powerful tool for troubleshooting Checkpoint VPNs.
Data science courses in Mysore
IKEVIEW is an incredibly powerful tool for VPN debugging, especially when working with complex IPSec tunnels. Its ability to parse and visually represent IKE logs makes identifying issues much faster and more efficient. It’s a real-time-saver compared to manually combing through raw log files, as it simplifies troubleshooting and enhances understanding of VPN mechanics at a deep level.
Thank you for the brilliant content.
Data science Courses in Germany
Data science is revolutionizing industries worldwide, and it's great to see that Iraq is now offering more opportunities to learn this valuable skill. If you're looking to dive into data science, this list of courses is an excellent place to begin your journey. Click here to find out more!
"This is so timely! The increasing interest in data science is clear, and offering courses in Iraq is a great way to empower future professionals. For anyone looking to get a head start in the field, I highly recommend checking out Data science courses in Iraq."
Great insights on troubleshooting Checkpoint VPNs using IKEVIEW! The step-by-step breakdown makes it easier to understand such a complex process. Your explanation of analyzing log files for root causes is particularly helpful.
Data science course in Bangalore
Great blog post! The step-by-step guide for troubleshooting Check Point VPNs is really helpful. I especially appreciated the clear explanations of common issues and how to resolve them. Keep up the awesome work.
Data science course in Gurgaon
This is such an insightful piece!
How Data Science Helps In The Stock Market
Thank you for this detailed guide on troubleshooting Check Point VPNs! Your step-by-step instructions and clear explanations make complex troubleshooting tasks much more manageable for network administrators.
Data science course in Lucknow
A handy troubleshooting guide for resolving Checkpoint VPN issues. A must-read for network administrators!
Data science course in Gurgaon
I really appreciate the clarity in this guide! The IKEVIEW troubleshooting tips are incredibly helpful for pinpointing issues quickly.
Data science course in Bangalore
This is exactly the kind of content I enjoy reading. Your tips on Troubleshooting Checkpoint VPNs with IKEVIEW are easy to understand and apply. Thanks for the trustworthy article.
Data Science Courses in China
"Great post! Your troubleshooting guide for Checkpoint VPNs is extremely useful for network administrators facing VPN-related issues. Thanks for sharing these practical tips to resolve common problems!"
Data science courses in Bangladesh
Troubleshooting Checkpoint VPNs with IKEVIEW involves analyzing logs to diagnose and resolve connection issues effectively. This tool helps identify misconfigurations, authentication problems, and encryption mismatches, ensuring secure and reliable VPN performance. Similarly, choosing elfliq nic salts provides vaping enthusiasts with a high-quality experience, ensuring satisfaction through informed choices. Both emphasize precision and attention to detail for optimal functionality
Great content about the troubleshooting and thank for sharing the information.
IIM SKILLS Data Science Course Reviews
Great guide! IKEVIEW is such a valuable tool for VPN troubleshooting. It’s incredibly helpful in breaking down the logs and pinpointing exactly where the VPN tunnel setup fails, whether it's Phase I or Phase II. The "No Proposal Chosen" and "Invalid ID Information" errors are easy to spot and can save so much time when diagnosing mismatches in configuration. The breakdown of both Main Mode and Quick Mode phases with detailed examples is especially useful. Thanks for sharing this detailed walkthrough! Investment Banking Course
A must-read for anyone curious about this topic. So well written
digital marketing courses in pune
Great post on using IKEVIEW for troubleshooting VPN connections.digital marketing courses in delhi
Troubleshooting VPNs can often be challenging, but this guide is clear and incredibly helpful. I especially appreciate the step-by-step instructions to resolve common issues. Thanks for sharing such valuable insights
Data science courses in pune
Using IKEVIEW for VPN troubleshooting simplifies the process of analyzing IKE.elg files, offering valuable insights into VPN connections. It’s a powerful tool for Checkpoint users, helping to quickly identify and resolve issues with VPN configurations.
Data science courses in Mumbai
Data science courses in Mumbai
Name: INTERN NEEL
Email ID: internneel@gmail.com
Great article on troubleshooting Checkpoint VPNs with IKEVIEW! digital marketing courses in delhi
Troubleshooting Checkpoint VPNs with IKEVIEW is a highly effective method for diagnosing VPN connectivity issues. This tool deciphers IKE and IPsec logs, helping identify negotiation failures, authentication problems, or encryption mismatches. By providing detailed insights into tunnel creation, it allows network administrators to pinpoint and resolve issues quickly. Mastery of IKEVIEW significantly enhances troubleshooting efficiency, ensuring secure, uninterrupted VPN communication for seamless remote access and data exchange across distributed networks.
Thank you.
digital marketing course in Kolkata fees
Very detailed and elaborative explanation on IKE.elg output. Thanks for simplifying the complex topics.
technical writing course
I really appreciate for your efforts you to put in this article, this is very informative and helpful. I really enjoyed reading this blog. Keep sharing and give us updates.
digital marketing course in coimbatore
Very interesting blog which helps me to get the in-depth knowledge about the technology, Thanks for sharing such a nice blog..
Data Science Courses in Micronesia
https://iimskills.com/data-science-courses-in-micronesia/
Data Science Courses in Micronesia
I want to appreciate your detailed explanations and troubleshooting steps make the process more manageable. Thanks for sharing this valuable information.
Data Science Courses in Micronesia
https://iimskills.com/data-science-courses-in-micronesia/
Data Science Courses in Micronesia
Troubleshooting Checkpoint VPNs with IKEVIEW is an efficient way to identify and resolve connection issues. Analyzing logs and IKE negotiations helps pinpoint misconfigurations, authentication failures, or phase errors. The tool’s detailed insights into VPN traffic make it indispensable for network admins, ensuring secure and reliable VPN connectivity. Mastering IKEVIEW simplifies complex troubleshooting, saving time and reducing downtime in critical environments.
Thank you for the post.
business analyst course in bangalore
"Excellent troubleshooting guide for Checkpoint VPNs! Your detailed steps and explanations are invaluable for resolving common VPN issues. Thanks for sharing your expertise!"
business analyst course in bangalore
Great guide on using IKEVIEW for VPN troubleshooting! It’s an invaluable tool for dissecting IKE traffic and understanding issues in both Phase I and Phase II of VPN connections. The detailed explanations of common errors like "No Proposal Chosen" and "Invalid ID-Information" are especially helpful for pinpointing configuration problems. Definitely a must-have resource for Checkpoint users!
digital marketing course in nashik
Wow it is really wonderful and awesome thus it is very much useful for me to understand many concepts and helped me a lot. Data science courses in France
thanks for sharing the article!
digital marketing agency in nagpur
Wonderful article thank you for sharing.
Medical Coding Course
IKEVIEW is a valuable tool for VPN debugging, providing detailed insights into IKE negotiations, authentication issues, and encryption failures, aiding efficient troubleshooting.
Medical Coding Course
Thanks for sharing these troubleshooting tips for Check Point VPNs! The step-by-step guide is really helpful for identifying and resolving common issues.
Medical Coding Courses in Chennai
Thanks for sharing these troubleshooting tips!
I've been struggling with our Check Point VPN and this been incredibly helpful.
Medical Coding Courses in Chennai
This blog gives us the procedure to use IKEVIEW for VPN troubleshooting.
Medical Coding Courses in Bangalore
IkeView is an offline viewer for the files generated with VPN debug and ike debug commands "vpn debug on" and "vpn debug ikeon" or a combo command "vpn debug trunc".This blog gives information on the troubleshooting issues.
Medical Coding Courses in Bangalore
QuickBooks accounting software program is simply manufactured by the Intuit for small and medium-sized businesses. With this specific best and inclusive accounting software, it is simple to and quickly track your company all income and expenses, efficiently track your payments, sales, and inventory, simply store your web visitors and vendors all information and a whole lot more things.
Medical Coding Course in Hyderabad
Thanks for sharing! IKEVIEW is a practical tool, with clear steps for analyzing issues in Phase I and Phase II. It is helpful!
Medical coding courses in Delhi/
"IIM SKILLS helped me gain the necessary skills to become a certified digital marketer. The hands-on approach helped me apply concepts immediately."
"The assignments were highly relevant, and the support provided by IIM SKILLS was outstanding. I was guided every step of the way."
Medical Coding Courses in Coimbatore
"The assignments in the Digital Marketing course at IIM SKILLS helped me build a strong portfolio, and I’m now confident in my digital marketing skills."
Medical Coding Courses in Coimbatore
Great insight! IKEVIEW is an excellent tool for troubleshooting VPN issues on Checkpoint firewalls. configuration!
Medical coding courses in Delhi/
IIMs have a strong emphasis on personal growth. Throughout my journey, I was constantly challenged to step out of my comfort zone and grow as an individual.
Medical Coding Courses in Chennai
Such valuable insights! I feel more confident about the topic now.
Medical Coding Courses in Chennai
"I love how you mix facts and personal experience. It really makes the content relatable." Medical Coding Courses in Delhi
Very informative! I really appreciate the insights.
Medical Coding Courses in Delhi
Another fantastic post! I can always count on your blog for the latest insights." Medical Coding Courses in Delhi
Thank you so much for sharing the informative article share with us, your blog was creative writing ability has inspired me.
https://iimskills.com/medical-coding-courses-in-bangalore/
Awesome Post!
Medical Coding Courses in Delhi
Greate Post. Keep Posting like this.
Medical Coding Courses in Bangalore
Nice blog, thanks for the information
Medical Coding Courses in Delhi
Nice tutorial. Thanks for sharing the valuable information. it’s really helpful. Who want to learn this blog most helpful. Keep sharing on updated tutorials…
https://iimskills.com/medical-coding-courses-in-hyderabad/
Great post! I’ve been exploring ways to build Part Time Income, and recently came across Udyogdhan. It’s been super helpful in developing practical digital skills that actually lead to real earning opportunities. If anyone’s looking to start something flexible and skill-based, it’s definitely worth checking out.
Wonderful Blog!
Medical Coding Courses in Delhi
wow amazing article, really liked it
https://iimskills.com/medical-coding-courses-in-hyderabad/
Thanks for the practical advice
Medical Coding Courses in Bangalore
Nice Post! Thank you for sharing knowledge, it was very good post to update my knowledge and improve my skills. keep blogging.
https://iimskills.com/medical-coding-courses-in-bangalore/
nice article i really liked.
Medical Coding Courses in Delhi
The Institute is contributing to the creation of knowledge and offer quality program to equip students with skills .
Data Science Courses in India
Great article very useful. Thanks for the share.
technical writing course
Using IKEVIEW for VPN debugging is a helpful tool for troubleshooting IKE (Internet Key Exchange) negotiations on Checkpoint firewalls.
https://iimskills.com/data-science-courses-in-india/
Nice article.
Data Science Courses in India
Nice and informative blog.
Data Science Courses in India
This guide on using IKEVIEW to troubleshoot Checkpoint VPNs is incredibly helpful. It demystifies a complex process with clear instructions and practical tips. A must-read for network admins and security pros dealing with VPN issues. Well-structured, detailed, and a great tool for effective VPN diagnostics and resolution.
Data Science Courses in India
The article likely does a great job of highlighting how IKEVIEW provides that much-needed visibility into the often-opaque world of IKE negotiations. Being able to see the specific proposals, exchanges, and potential errors in real-time can drastically cut down troubleshooting time.
Data Science Courses in India
The course includes training in coding for skilled nursing facilities.
Medical Coding Courses in Delhi
Their exam preparation module helped me a lot.
Medical Coding Courses in Delhi
IKEVIEW step wise explained...I Thanks for another great one!
Medical Coding Courses in Vadodara"
Thank you for your informative content. Visit our website at Best AI course in Coimbatore | 100% Job Placement Assistance | Learn English & Tamil | Internship Program
Very inspiring and motivational. Medical Coding Courses in Vadodara
Troubleshooting Checkpoint VPNs using IKEVIEW involves analyzing IKE logs to identify handshake failures, authentication errors, or configuration mismatches. IKEVIEW decodes complex log files, helping admins pinpoint issues in VPN tunnels quickly, ensuring secure and reliable connections. This tool is essential for resolving Checkpoint VPN connectivity problems efficiently.
Data Science Courses in India
Thank you for this practical guide on troubleshooting Check Point VPNs using logs! Your step-by-step approach and tips for interpreting log files make resolving VPN issues much more manageable. This is a valuable resource for network administrators dealing with Check Point environments. Appreciate you sharing your expertise!
Medical Coding Courses in Delhi
Great troubleshooting tips! VPN issues can be really tricky, so having clear guidance like this is super useful. Thanks for sharing your experience with Check Point VPNs!
Medical Coding Courses in Delhi
Very practical VPN troubleshooting tips.well explained!
Medical Coding Courses in Kochi
Very useful guide! The steps are clear and make VPN debugging with IKEVIEW much easier to understand. Thanks for sharing!
Medical Coding Courses in Delhi
Thank you for this comprehensive guide on troubleshooting Check Point VPNs using IKEView. Your step-by-step instructions for capturing and analyzing IKE logs are incredibly helpful.
Medical Coding Courses in Kochi
Thank you for this poignant reflection on Bracknell's town centre transformation. Your words capture the bittersweet emotions many feel as familiar landmarks give way to modern developments. It's a reminder of how urban renewal can both revitalize and reshape community identity.
Medical Coding Courses in Kochi
Thanks for the Valuable information. ReallyMedical Coding Courses in Delhi useful information. Thank you so much for sharing. It will help everyone
This is an excellent guide for using IKEVIEW to troubleshoot VPN issues on Check Point firewalls—clear, detailed, and full of practical examples. Medical Coding Courses in Kochi
Thank you sir And keep it up More Post And Its A Awesome Web page sir Thank You So Much ,
Medical Coding Courses in Delhi
Great step-by-step guide for using IKEVIEW! It really helps understand VPN troubleshooting with Checkpoint firewalls.
Medical Coding Courses in Delhi
Helpful guide to troubleshoot VPNs—well explained.
Medical Coding Courses in Kochi
Informative guide on troubleshooting Check Point VPNs with IKEVIEW—very helpful!
Medical Coding Courses in Kochi
Amazing writeup. Thank you for sharing this step-by-step tutorial on troubleshooting VPNs with IKEVIEW.
Medical Coding Courses in Kochi
This is most informative and also this post most user friendly and super navigation to all posts... Thank you so much for giving this information to me..
Medical Coding Courses in Delhi
Thanks for sharing this information admin, it helps me to learn new things. Continue sharing more like this.
Medical Coding Courses in Delhi
Nicely put—your tone makes this super approachable.
Medical Coding Courses in Delhi
Thanks for the practical VPN troubleshooting guide using Check Point’s tools—the clear step-by-step diagnostics make resolving connectivity issues much easier. Well-explained and developer-friendly!
Medical Coding Courses in Delhi
This really helped me see the topic differently.Medical Coding Courses in Delhi
Excellent breakdown of VPN debugging with IKEVIEW—super useful for identifying Phase I and Phase II issues. Thanks for the detailed guide!
Medical Coding Courses in Delhi
Really helpful VPN troubleshooting tips for Check Point—your examples with IKEView make diagnosing tunnel issues much easier to grasp!
Medical Coding Courses in Delhi
This is a solid, practical guide for anyone troubleshooting Checkpoint VPNs. IKEVIEW can feel daunting at first, but your breakdown—especially of the Main Mode packet sequence—is clear and useful. Highlighting the "No Proposal Chosen" issue with real context helps demystify common Phase I failures. Great resource for network admins working with Checkpoint gear.
Medical Coding Courses in Delhi
Great guide on using IKEVIEW for Checkpoint VPN troubleshooting! Clear steps and explanations make it easy to follow and resolve common VPN issues quickly. Thanks for sharing!
Medical Coding Courses in Delhi
Thanks for sharing this in depth troubleshooting guide, Check Point VPNs can sometimes be complex to debug, and your step-by-step walkthrough
Medical Coding Courses in Delhi
It’s a practical guide for anyone dealing with VPN issues. Thanks for sharing this detailed walkthrough!
Medical Coding Courses in Delhi
For professionals looking to transition into high-demand roles in healthcare tech and administration, check out this well-reviewed resource on Medical Coding Courses in Delhi. It's a great way to build a secure and rewarding career path in a growing industry.
This blog is fantastic!
Medical Coding Courses in Delhi
Great post! IKEVIEW is such a powerful tool for diagnosing Checkpoint VPN issues. Your step-by-step guide makes troubleshooting much easier—thanks for sharing!
Medical Coding Courses in Delhi
Very helpful guide! IKEVIEW is a powerful tool for analyzing VPN issues in Checkpoint, and this post makes the troubleshooting process much clearer. Great resource for network admins!
Medical Coding Courses in Delhi
This is a thorough and incredibly helpful guide for anyone dealing with VPN issues in Checkpoint environments. The breakdown of IKEVIEW usage and interpretation, especially the Phase I and II explanations, is very clear. Thanks for sharing such a detailed and practical resource!
Medical Coding Courses in Delhi
Great troubleshooting tips using tcpdump for Check Point VPNs—super valuable for network admins diagnosing connectivity issues! If you're also exploring structured data roles in healthcare IT, consider checking out these Medical Coding Courses in Delhi for a meaningful way to apply your analytical skills.
Thanks for the detailed walkthrough! VPN troubleshooting can be complex, and tools like IKEVIEW make a big difference. For those exploring a career in medical data management, you might want to check out these Medical Coding Courses in Delhi – a great complement to healthcare IT.
Thanks for this detailed troubleshooting guide! VPN issues—especially with CheckPoint—can be notoriously tricky. Your breakdown of log analysis, policy verification, and common misconfigurations (like Phase 1/Phase 2 mismatches) makes the steps clear and actionable. This will definitely help sysadmins streamline VPN issue resolution. For readers pursuing structured, security-focused career paths, this might also be worth exploring:
Medical Coding Courses in Delhi
Excellent walkthrough! Troubleshooting Check Point VPNs can be complex, and your explanation of how to leverage Wireshark for packet analysis is incredibly helpful. The step-by-step guidance and screenshots make it easy to follow, even for those relatively new to VPN diagnostics. Thanks for sharing such a practical and informative resource—definitely bookmarking this!
Medical Coding Courses in Delhi
Thanks for the clear VPN troubleshooting guide! I particularly liked the step-by-step vpn debug and fw ctl zdebug examples—they make diagnosing IPSec issues much more approachable. Very practical—appreciate the share!
Medical Coding Courses in Delhi
thanks for sharing this information on Troubleshooting Checkpoint VPNs with IKEVIEW.
Medical Coding Courses in Delhi
Great, clear guide on troubleshooting Checkpoint VPNs with IKEVIEW! The tips for analyzing logs and common error fixes are really useful. Thanks for sharing! Do check out Medical Coding Courses in Delhi for more career opportunities.
This guide offers a detailed and practical walkthrough for diagnosing VPN issues using IKEVIEW. It’s especially helpful in interpreting IKE.elg logs and pinpointing Phase I and II failures
Medical Coding Courses in Delhi
Extremely helpful breakdown—thanks for demystifying VPN debugging in Check Point!
Your step-by-step use of vpn debug, combined with real log examples and clear interpretations, makes this post a valuable reference for both beginners and experienced admins. I especially liked the clarity on enabling/disabling debug and interpreting IKE/ESP negotiation failures—super useful in production environments.
Medical Coding Courses in Delhi
Thank you for sharing such great information very useful to us.
Medical Coding Courses in Delhi
You've anticipated my needs! Addresses concerns before I voice them.
Medical Coding Courses in Delhi
financial modeling courses in delhi
Really useful guide! Troubleshooting VPNs with SmartView Tracker can be confusing, but your explanation made it much easier to follow. I liked how you included real scenarios and detailed steps — it gave great clarity. Thanks for sharing such practical insights. This post is a big help for Check Point users!
financial modeling courses in delhi
Excellent resource! Troubleshooting VPN issues can be notoriously frustrating, and IKEVIEW is such a powerful yet underutilized tool in the Checkpoint ecosystem. Your walkthrough really helps demystify the process of parsing IKE and IPsec negotiations.
I especially liked how you explained interpreting the logs and identifying where the handshake breaks down. That kind of clarity is invaluable for admins trying to resolve tunnel failures under pressure.
Really appreciate the effort you put into this post! The insights are clear, helpful, and genuinely made me think. It’s always refreshing to come across content that’s both informative and engaging. Looking forward to exploring more from you!
financial modeling courses in delhi
financial modeling courses in delhi
IKEVIEW is such a powerful tool for diagnosing VPN issues on Check Point firewalls. Being able to analyze the IKE debug logs offline really helps pinpoint where negotiations fail—whether it's Phase I or Phase II. The visual breakdown of Main Mode, Aggressive Mode, and Quick Mode packets makes it much easier to interpret complex VPN behavior.
QuickBooks 2019 will be the better account management product till now. The recent improvement that is made in this program regarding current user requirements plus the methods to overcome the limitation of previous QuickBooks versions.
financial modeling courses in delhi
This article is an excellent guide for IT admins dealing with VPN connectivity issues in Check Point environments. Troubleshooting VPNs often requires not just technical know-how but also patience and a methodical approach. Your detailed explanation of logs, encryption domain mismatches, and phase 1/phase 2 negotiations is spot on. VPNs are the backbone of remote work security, and having reliable troubleshooting tips can save hours of frustration. This kind of step-by-step breakdown is incredibly useful for both beginners and experienced network engineers.
financial modeling courses in delhi
Really nice and interesting post. I was looking for this kind of information and enjoyed reading this one. Keep posting. Thanks for sharing.
href="https://iimskills.com/financial-modelling-course-in-delhi/">financial modeling courses in delhi
This is an incredibly detailed and practical guide for anyone dealing with VPN troubleshooting on Checkpoint firewalls. The step-by-step use of IKEVIEW and clear breakdown of both Phase I and Phase II IKE negotiations make it much easier to pinpoint common issues like “No Proposal Chosen” or “Invalid ID Information
https://iimskills.com/financial-modelling-course-in-delhi/
This guide on using IKEVIEW for troubleshooting Check Point VPNs is incredibly detailed and practical. The step-by-step instructions and clear explanations make complex VPN issues more accessible to resolve. A must-read for network professionals dealing with VPN configurations.
financial modeling courses in delhi
nice blog
href="https://iimskills.com/financial-modelling-course-in-delhi/">financial modeling courses in delhi
This is a fantastic troubleshooting resource for Checkpoint VPN configurations. VPN setup errors can be complex to diagnose, and your blog effectively simplifies common problems and solutions. It’s a practical guide that even seasoned network administrators can benefit from. Keep sharing these valuable insights!
financial modeling courses in delhi
I like how you explained this topic. It’s straightforward and easy to understand
https://iimskills.com/financial-modelling-course-in-delhi/
Thanks for explaining how to interpret IKE logs clearly—very useful for resolving VPN connection problems.
financial modeling courses in delhi
Excellent guide! IKEVIEW simplifies VPN diagnostics by parsing IKE.elg files, making it easier to identify issues in Phase I and II negotiations. A must-have tool for Check Point administrators.
financial modeling courses in delhi
Thank you so much for sharing the informative article share with us, your blog was creative writing ability has inspired me. financial modeling courses in delhi
Clear and practical guide! The walkthrough on using IKEVIEW for troubleshooting Checkpoint VPNs is especially valuable for quickly identifying and resolving connectivity issues.
financial modeling courses in delhi
Your clear explanation of troubleshooting Checkpoint VPNs with IKEVIEW makes the process easier to understand. The step-by-step method offers practical guidance that network professionals can apply right away. This knowledge will help many resolve VPN issues quickly and keep systems running smoothly.
financial modeling courses in delhi
Thanks for breaking this down so clearly! VPN debugging can get pretty overwhelming, but your step-by-step explanation of IKEVIEW and the common errors makes it much easier to follow. The real-world examples of Phase I and Phase II failures are especially helpful.
financial modeling courses in delhi
Great resource for anyone working with Checkpoint VPNs! Using IKEVIEW for troubleshooting is a game-changer—it really helps visualize and analyze IKE negotiations in detail. This kind of clarity makes diagnosing VPN issues much more manageable. Thanks for sharing such a practical guide!
financial modeling courses in delhi
Really helpful breakdown! When I’m looking at IKEView traces, I always remind myself to read it like a conversation between two peers. Phase 1 is all about agreeing on how to talk (encryption, hash, DH), and if I see a ‘no proposal chosen’ there, I know the settings don’t line up. Once Phase 1 is green, Phase 2 is where the actual traffic negotiation happens — that’s where proxy IDs and encryption domains usually trip things up. I also watch for repeated retransmits in the frames, since that often points to routing or firewall drops rather than a config mismatch. IKEView makes it much easier to follow the story frame by frame and pinpoint exactly where the negotiation falls apart.”
financial modeling courses in delhi
Great job on covering troubleshooting Checkpoint VPNs with IKEVIEW! Your detailed approach helps demystify the complexities of VPN troubleshooting. It's essential knowledge for network professionals, and your insights will definitely assist many in overcoming their challenges. Keep sharing your expertise!
"mern stack course in bangalore,
mern stack developer course in bangalore,
mern stack training in bangalore"
Excellent breakdown for beginners. A key tip I’d add: always make sure you are running the command on the correct security gateway itself, not the management server!
VISA Management Courses in Delhi
Thank you for sharing such a useful information.Keep posting.Looking forward to read more.
ABAP WebDynpro Online Coaching In Australia
SAP Workflow ABAP Training
Guidewire Claimcenter Online Course from India
SAP IS Retail Online Training from USA, Uk, Australia, UAE, Canada
Thank you for sharing the information.Looking forward to read more.
C & C++ Language Online Training from USA
Microsoft Azure Training Institute In Hyderabad
Best Angular JS Training from South Africa
Web Development Online Classes
Manual Testing Training Institute In Bangalore
Tibco BW 6 Online Training from Chennai
Teradata SQL Training Course In Hyderabad
tableau software learning helps you transform raw data into clear, interactive visual insights.
With hands-on practice, tableau software learning builds skills for smarter analysis and storytelling.
Master the principles of UI/UX Design with OnlineITGuru. Learn to design user-friendly, visually appealing interfaces using tools like Figma and Adobe XD, and gain hands-on experience creating prototypes and wireframes.ui ux design course online
"Enhance your skills with sfdc admin training designed for aspiring Salesforce administrators. Gain hands-on experience in managing users, customizing apps, and automating workflows efficiently."
Explore data visualization and analytics through hands-on practice with tableau software learning
Build interactive dashboards and gain practical insights that turn raw data into clear, impactful stories with tableau software learning.
power bi online training helps you learn how to analyze data, create interactive dashboards, and share insights effectively.
Learn data visualization and analytics withpower bi classes online designed for beginners to advanced professionals.
salesforce administrator classes provide hands-on training to manage users, customize workflows, and maintain secure, scalable CRM systems.
Master data visualization with tableau course online designed for beginners and professionals alike.
Master salesforce dev training to build, customize, and deploy powerful Salesforce solutions with confidence.
Post a Comment