Overview
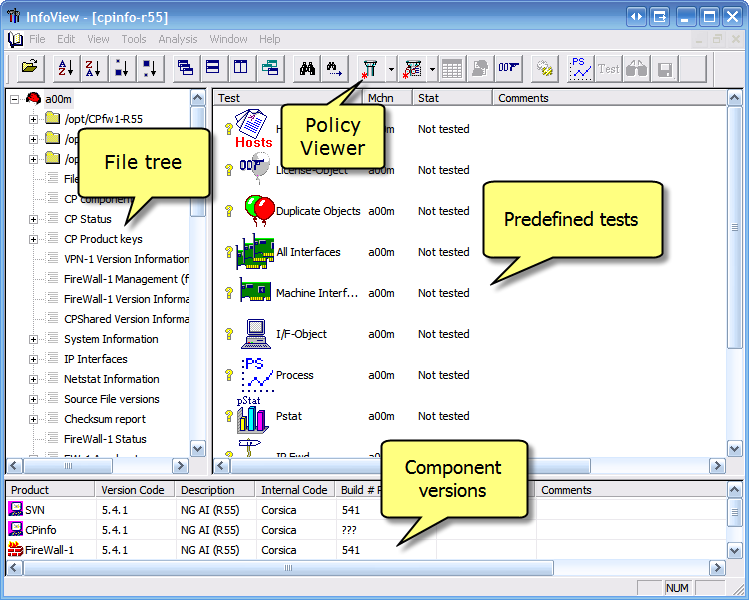
- The left pane shows the data tree, which holds a hierarchical list of input data, consisting of file and directories, in addition to other text sections.
- The right pane shows a list of tests that can be applied on the input files.
Basic actions
There are 3 ways to open a text file or a text section:
- Double-click the text file/section.
- Right-click the text file/section and select 'Open'.
- Drag and drop the text file/section into an open window of any text editing software (e.g., Notepad, Word).
Copy file/text section/folder
You can copy a text file, text section, or folder to any Windows folder directly from InfoView. To do this, either drag and drop the file/folder, or copy and paste it.
View the Policy in the Policy Viewer (SmartDashboard)
To better understand the gateway's set-up, and especially the policies, InfoView lets you view the CPInfo information in SmartDashboard on your desktop.
Note: This is possible only if the CPInfo output file is from a management server (i.e., Security Management/SmartCenter/Provider-1/Standalone).
- Make sure you have the corresponding customer version of SmartConsole installed.
- In InfoView, click the Policy Viewer button (see in above picture), or select 'Tools' > 'Policy' from the main menu. It might take a few minutes for SmartDashboard to show. If required, manually configure the location of different SmartDashboard versions in InfoView - select 'View' > 'Options', go to the 'Directories' tab.
Viewers
| Info Tab - Kernel table viewer | |
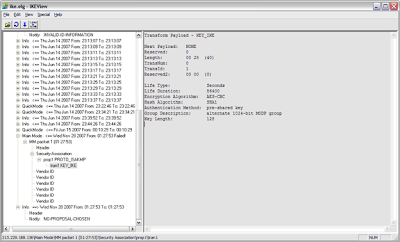
| IKEView | |
 | LicView - Check Point License string viewer |
| Process Viewer |
Advanced actions
There are 2 sorting options for the data tree:
 - Alphabetically.
- Alphabetically. - By file size.
- By file size.
To search for text in the data tree, either click the 'Find' button on the main toolbar, or use the keyboard shortcut Ctrl+F.
Click the 'Find next' button, or press F3 to repeat the previous search.
Export Object File
You can remove all certificate keys from the object file (
objects_5_0.C) that is imbedded in the input file. To do this, from the main menu, select 'File' > 'Export object file (fresh CA)' and save the new file.Analysis pane
To run a test, either double-click it, or select it and press the 'Test' button.
To see the test results after it has finished running, either double-click it, or select it and press the 'View' button.
Possible test statuses:
| OK | Test Passed |
| Suspicious | Possible problem (test this issue manually) |
| Irrelevant | This test is irrelevant to the given input file |
| Not Tested | This test has not been executed yet |
Icon legend
| Text section | |
| Text file | |
| Text file (Unavailable - not collected) | |
| Text file (Soft Link) | |
| Text file (Registry) | |
| Text File (WinMSD) | |
| Folder | |
| Root Icon - Firewall is installed | |
| Root Icon - Meta IP is installed | |
| Root Icon - Provider-1 is installed | |
| Root Icon - SecureClient is installed |
Data tree
To see the server information, right-click the server name (the root of the tree) and select 'Properties'.
Here you can see the server version, if the server is a Security Gateway or Security Management and more.
$FWDIR directory
The tree shows the
$FWDIR directory collected by the CPInfo utility from the server. Here you can find some useful files, such as:- In the
confdirectory:objects_5_0.C- Full database objects file.fwauth.NDB- All users the administrator defined on the SmartDashboard.fwauthd.conf- Configuration file of the Security Servers.asm.C- IPS configuration file.classes.C- Definitions of the fields in the CP Database files.
- In the
logdirectory:fwd.elg- fwd process log file. In the output file, you can find any messages that may have occurred on or about the time a problem was identified. Dates are associated with messages in the file.fwm.elg- fwm process log file.
- In the
databasedirectory, you can see all of the relevant policy files for the Security Gateway.
The tree shows the
$CPDIR directory collected by the CPInfo utility from the server.Here you can find some useful files, such as:
- In the
logdirectory:cpd.elg- CPD log file. Shows useful information about SIC related issues, CP WatchDog log files (cpwd.elg), processes crashes and more.
- In the
registrydirectory:HKLM_registry.data- Shows all products and fixes installed on the system.
- CP components - Shows overview information about the products installed on the system (such as Acceleration [PPACK], Advanced routing [ADVR], etc.). Might be useful for comparing cluster members.
- CP Status - Shows policy name and install time, FW connections and packet statistics (per interface as well).
- FireWall-1 Version Information - Shows the FW & OS patch level including HFAs.
- System Information:
date- Date and time on the machine when the CPInfo was collected (useful for sync issues and logs referral).ethtool- Interface configuration and status.ethtool -i- Interface driver version.uname -a- OS information, date of OS kernel compilation.uptime- When the system was last rebooted.ps auxww- Processes list (CPU/Memory consumption, PID, full process path).vmstat 1 10- Machine CPU consumption. User/Kernel space (us=user space, sy=kernel space, id=idle cpu).top -n 2- System resources usage. Overview: system (kernel), user, softirq (CPU software interrupts), iowait (HD operation), memory usage status, and processes list (as inps auxww).env- Environment variables.df -k- Hard disk space information.- Package Manager Report (RPM) - Output of rpm -qa command. List of RPMs installed.
- List PCI devices (
lspci -nv) - list of hardware devices. Class 0200 stands for Interface Card (NIC). Class and Subsystem information will assist you to identify the exact NIC model in the PCI IDs list . See theHardware Compatibility List to make sure the NIC is supported. - Interrupts Information (
/proc/interrupts) - Hardware device per IRQ list. - Memory Information (
free -k -t) - Free memory available. Calculated as explained in sk32206. - Loaded Modules (
lsmod) - List of kernel modules currently loaded (FW, VPN, acceleration kernel modules, interface drivers, etc). - Additional Memory Information (
meminfo) - Output ofcat /proc/meminfo. for additional memory details such as 'HighTotal' > high kernel memory allocated by the OS during reboot. - Additional CPU Information (
cpuinfo) - Output ofcat /proc/cpuinfo. Specifies the CPU vendor and model, and number of processors. - System's Hardware - Server vendor and model details, bios details.
- IP Interfaces:
ifconfig -a- Full details about the interfaces: MAC, MTU, IP, Mask, etc. Can assist in identifying the master in a VRRP cluster (only the master has 'vrrpmac' addresses in this output.fw ctl iflist- Interfaces mapping to the IDs given by the OS during boot. In the kernel debug's output, the interfaces are identified with those IDs, instead of the interfaces' names.fw getifs- Summary display of IP addresses per interface.
- Netstat Information:
netstat -rnv- Full routing table (for routing/advanced routing troubleshooting, cluster members comparison).netstat -i- Interface packets statistics, RX/TX drops and errors per interface.netstat -s- OS statistics per protocol (ICMP, IP, UDP, TCP).netstat -nap- List of open (listening) ports per process, and established connections per process (helps to identify which process is occupying each port at the time the CPInfo was collected).arp -a- ARP table output. Use the MAC addresses to crossover information with traffic captures. If the word "Incomplete" is shown in the output file, it may be an indication that automatic ARP is not working.
- FW-1 Accelerator - Acceleration device (SecureXL/PPACK) status, build, statistics, accelerated connections and SIM affinity information. "accel packets"/"F2F packets" ratio will give you indication regarding acceleration efficiency. SIM affinity customization can increase performance as well - see sk33506.
- FireWall-1 Tables - Short Format - Output of
fwtab -t-s, list of all kernel tables (connections table ['connections' / ID 8158], NAT table ['fwx_alloc' / ID 8187], etc) and current value of each table (#VALS column).
- FireWall-1 Statistics (
fw ctl pstat) - The last parameter in the output file is State Sync (used for Cluster troubleshooting). It show 'off' when it is off, and shows packets statistics when it is on.- FireWall-1 Debug (
fw ctl debug) - Shows which kernel debug flags are on.- FireWall-1 Chain/Connections Modules - Output of 'fw ctl chain/connections', list of loaded FW chains (corresponds with installed products). Must be identical between cluster members.
- Overlapping Encryption Domains - Might cause VPN related issues.
- High Availability - Clustering-related information
- High Availability State (
cphaprob state) - Indicates the cluster mode, the status of the cluster member itself and how this cluster member perceives the status of other cluster members. View and compare statuses of each cluster member. - High Availability -i list (
cphaprob -i list) - View a Pnote "device" that may be in a problem state. Cluster member status is 'down' when a Pnote is in 'Problem' state. - High Availability interfaces (
cphaprob -a if) - This output file shows the status of the interfaces for that cluster and VIP addresses, and CCP mode of the interfaces. The number of "Required interfaces" (determined during boot) and the CCP mode (multicast/broadcast) must be the same on both members. - High Availability SyncStat (
cphaprob syncstat) - Synchronization statistics - refer to Cluster Admin Guide for output analysis in order to tell if there is a sync related problem.
- VSX Information (CTX 0) [on a VSX machine] - Contains information about the CTX IDs (VS IDs), status and policy details of the VSX physical box and of the Virtual Devices.
- CP License - Output of
cplic print, license information. Using the wrong license might cause unexpected behavior.- CPWD (Watch Dog) information - Output of
cpwd_admin list, list of all processes monitored by CP Watchdog and their status.DLL_EXEC_Kernelversions - Current builds of system files. You can use this information to check the current builds and to verify if provided Hotfix replaced the files it should.- DLL versions - Current build of library files (
$FWDIR/lib). - EXEC versions - Current build of binary files (
$FWDIR/bin). - Kernel versions - Current build of kernel modules files ($FWDIR/boot/modules).
/var/log/messages:- When no buffer is defined in kernel, system messages are sent directly to the OS.
- We refer to these as "console messages" since in most OSs the messages are printed to the console and copied to
/var/log/messagesor/var/adm/messages. - This is why error messages (which are generated out of debugging context) are sent to the console.
- When generated in debugging context, error messages are not directed to the console but to the debug buffer, together with all other messages.
- In Windows, "console messages" in fact appear in the event viewer.
/var/log/routing_messages- Advanced routing error messages, search for errors when troubleshooting dynamic routing (GateD) related issues./etc/resolv.conf- DNS configuration file./etc/hosts- IP address per hostname mapping. In a cluster environment, misconfiguration of this file might cause unexpected behavior. See sk42952./etc/sysconfig/ethtab- Interface name per MAC address, OS mapping./etc/sysconfig/netconf.C- OS interfaces and routing configuration file. Compare it to /etc\sysconfig/ethtab when troubleshooting IP/MAC address mismatches.Disabling SmartMap before launching the Policy Viewer
SmartMap can make SmartDashboard crash or hang for a long time before SmartDashboard launches from InfoView.
To disable SmartMap:- Open the CPInfo file in a text editor.
- Find and replace all instances of:
totally_disable_VPE (false)
Tototally_disable_VPE (true)
(The value is defined in theobject_5_0.C file). - Save a copy of the edited CPInfo file.
- Re-open it in InfoView.
InfoView for Provider-1 (pInfoView)
Use the pInfoView tool to view a CPInfo output file collected from a Provider-1 server (MDS level).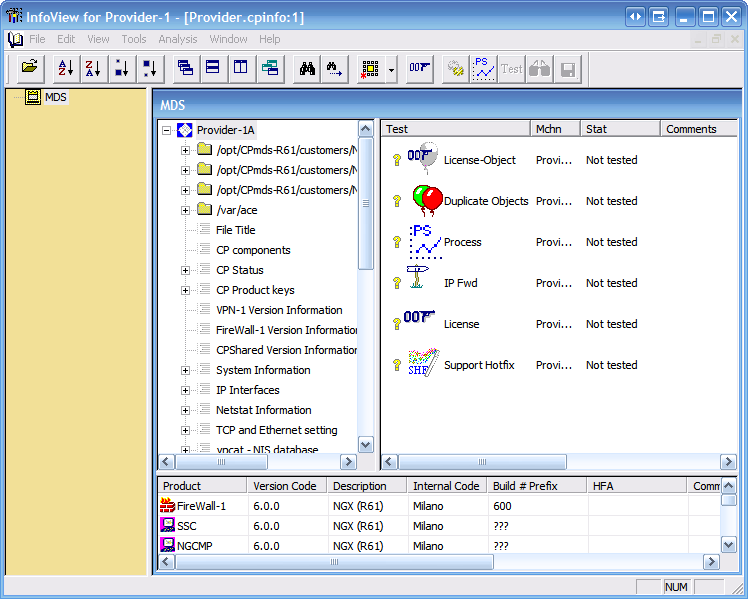
- The Left pane shows a list of all of the CMAs, arranged under the MDS. The grayed out CMA icons represent CMAs that were not collected by the CPInfo utility.
- The consists of two sub-panes:
- The left sub-pane shows the data tree, which holds a hierarchical list of input data, consisting of file and directories, in addition to other text sections.
- The right sub-pane shows a list of tests that can be applied on the selected MDS/CMA.
Icon legend
In addition to the icons that are listed above, pInfoView includes these 3 icons:
MDS - Selecting this icon changes the context of the right pane to MDS 
CMA - Selecting this icon changes the context of the right pane to this CMA 
CMA (Unavailable) Configuring InfoView to use a specific text editor
Procedure:- Open InfoView.
- From the main menu, select 'View' > 'Options'.
- Under 'File Editor', select 'user defined'.
- Click 'Browse' and select your preferred text editor.
- Click 'OK'.
- FireWall-1 Statistics (